Overview in PDF form
System Components

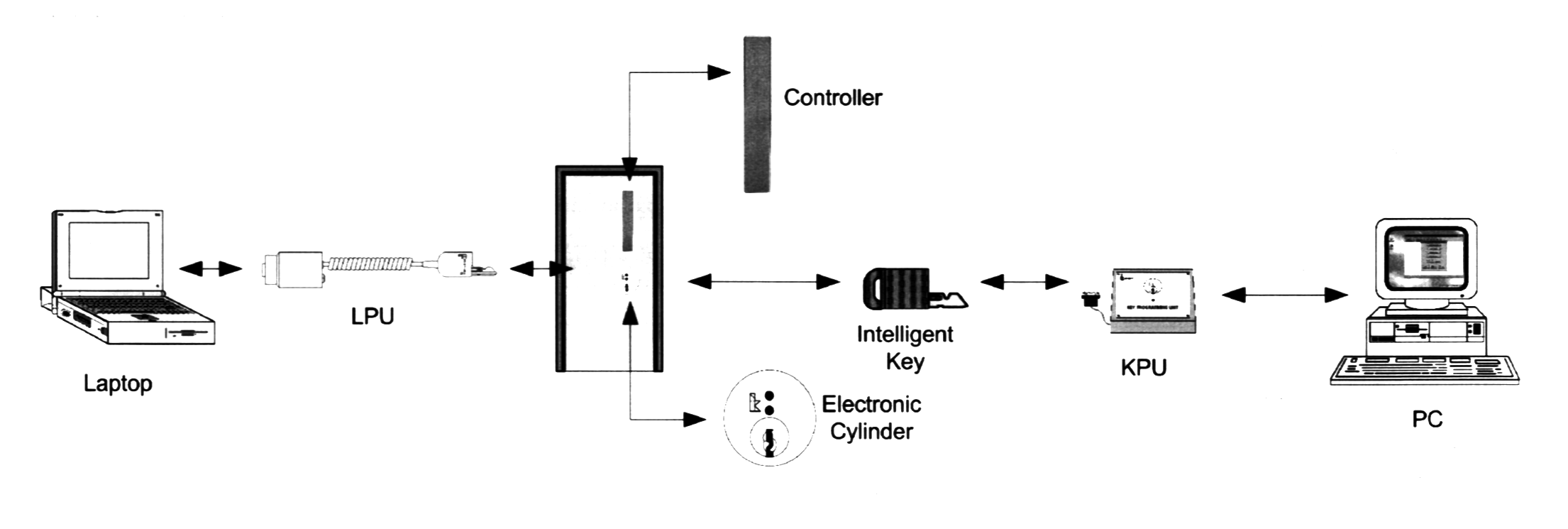
The Intelligent Key is the heart of the INTELLIKEY system. The key carries the access control and personal identity data of the assigned keyholder. Each INTELLIKEY key may be reprogrammed hundreds of times, allowing it to serve many keyholders and many functions. It cannot be read or duplicated except by authorized personnel equipped with site-specific INTELLIKEY equipment.

The Intelligent Lock Controller is the decision-making component of the INTELLIKEY system. The controller's sophisticated microcomputer is programmed with the access information for the door it controls. The electronic controller communicates with the Intelligent Key to read the key's programmed access information. If the key is granted access, the controller board's output circuitry activates the appropriate locking mechanism to allow the keyholder entry. The electronic controller has a built-in clock and calendar, allowing it to control access by time as well as location. This provides features such as time zones, holidays, and expiration dates. The controller automatically adjusts its clock for leap years and for daylight savings time. The controller's memory also retains an audit trail of the keys that have been used in it. There are controller housings available to fit any mounting arrangement.

The Electronic Cylinder provides the link between the INTELLIKEY controller and key. INTELLIKEY controllers and keys communicate through an invisible, encrypted infrared link provided by the cylinder. INTELLIKEY cylinders are available as replacements for most standard cylinder types, including mortise, rim, and European profile. The electronic cylinder may be configured for either rotating or fixed operation. The Rotating Cylinder is used in conjunction with new or existing mechanical locking devices where rotation of the cylinder retracts or throws a latchbolt. These locking devices include traditional mortise locks, panic devices, deadbolts and key switches. The Fixed Cylinder works as a key reading device only and is used in conjunction with devices such as parking gates, elevators, turnstiles, electric locks, electric strikes, and magnetic locks.

The Key Processing Unit interfaces with a personal computer and transfers data to and from the electronic key. The KPU is used for programming and updating user keys, and for interrogating keys to read authorization or audit trail information. The KPU connects directly to a PC for local key programming, or through a network for programming or interrogating keys at a remote site.

The Lock Programming Unit interfaces with a personal computer and transfers data to and from the electronic controller. The LPU is one method for programming and updating INTELLIKEY controllers. A Lock Programming Unit may be used in conjunction with a laptop computer to form a portable controller update or interrogation unit.
The INTELLIKEY programming software, Quantum Plus, maintains a database of the features selected for each key and controller in your system. This Microsoft Windows based software system simplifies the task of programming controllers, issuing and tracking keys, and maintaining access control within your site. Quantum Plus is available in both a standard version for institutions that maintain their own keying systems, and a multi-site version for INTELLIKEY suppliers who support several smaller sites.
Controlling Access
Site Codes
INTELLIKEY's Electronic Site Code feature guarantees that only the keys you issue for your site will be granted access to your doors. The Site Code is a unique digital code programmed into the memories of each key and controller. This serves the same purpose as the custom keyways used in mechanical keying systems, but provides much higher security. If the key's Site Code doesn't match that of the controller, the key will not be granted access. This ensures that keys issued at another site - no matter where in the world it's located -- will never open your doors. Furthermore, the Key and Lock Programming Units must also be programmed with the same Site Code before they can read or update your keys and controllers. This prevents an unauthorized individual from stealing a key and attempting to crack your keying system by examining the information in the key.
Authorizing Access
Access rights can be added to an INTELLIKEY system through either the controller or key. A new controller is programmed to grant access to existing keyholders. A new key is programmed to automatically grant itself access the first time it is used in authorized controllers. This eliminates the need to manually update controllers when new keyholders are added, or to recall keys when new controllers are added to your site.
System Features
INTELLIKEY's Quantum software maintains a database of the features selected for each key and controller in your system. Quantum interfaces with the Key and Lock Programming Units to transfer programming information to the controllers and keys.
Electronic keys are programmed using the KPU unit connected to a personal computer. The KPU allows a locksmith or access control manager to easily issue keys, and to change features and access rights for individual users as the need arises. The KPU also allows you to interrogate users' keys, to determine such information as where a key has been used, and when.
Controller programming may be accomplished by two methods. The initial programming of an INTELLIKEY controller is done using the Lock Programming Unit. This device provides a link between a personal computer and the controller, and is typically used for programming controllers prior to their installation. The Quantum software system also allows you to produce Controller Update Keys which, when inserted in a controller, reprogram the characteristics of the controller.
Activation and Expiration date
The key may be programmed with dates to determine a time frame during which it will be allowed to operate. This feature would be used for construction keying, or in a hotel or student dormitory, where it is desirable to have the key cease functioning after a specific date if it is not returned.
Holidays
Each key may be programmed for 16 periods of up to 120 days apiece during which it will not operate. These may be holidays or days when the keyholder's place of employment is closed.
Daylight Savings Time adjustment
The controller may be programmed to automatically adjust its clock by one hour at the beginning and ending of Daylight Savings Time. The beginning and ending dates and times may be programmed for up to 3 years in advance.
Time Zones
Time zones define specific periods of time during which a key is allowed to operate. A time zone may cover only a few hours, such as a normal work shift, or may cover several days. Each door to which a keyholder has access may be linked to one of the time zones. For example, a user may be able to unlock the front door of the building at any time, the computer room only from 7 AM to 5 PM Monday through Friday, and the break room only from noon until 2 PM on weekends.
Scheduled Unlock
The controller may be programmed to automatically unlock itself at a specified time, then automatically re-lock at a later time. This feature is useful for the front door of a building to which a large number of people need access. The Scheduled Unlock function can be restricted to not work on holidays. The controller also features a First-Man-In function that requires that a legal key be inserted in the controller on any given day before the controller will automatically unlock. This prevents unlocked doors on days with inclement weather when no employees have made it to work.
Audit Trail
The controller may be programmed to record key accesses, and thus provide an audit trail of keyholders who have used the door. The information recorded includes the key identification, the date, and the time. Keys may be programmed to record an audit trail of which controllers they have been used in, including the date and time.
AREST®
The Automatic Restraint function allows both the controller and key to monitor the illegal (unauthorized) access attempts in which it is involved. When either device reaches a selectable limit for illegal accesses, the controller will take protective action by disabling the key. The controller also records the key identifier, date, and time in its memory, and the controller identifier, date and time in the key's memory. A disabled key must be reset using the KPU before it can be used again in a controller. A disabled controller must be reset using an LPU before it can be operated with a key.
INTELLIKEY System Capacities
| Controllers in System | 4000 | |
| Keys in System | 10000 | |
| Audit Trail in Controller | 1000 keys | |
| Audit Trail in Key | 45 doors | |
| Time Zones | 2 per key |